Offensive Security Notes
Unorganized collections of my notes from CTFs and penetration tests
1. Search for whitelisted applications when looking to migrate and dump credentials. During a penetration test I was struggling to dump credentials with Kiwi as a PoC. Migrating into an AppSense application that is required to be whitelisted by endpoints can result in easy l00t. This link lists a few of the executables that I was able to migrate into with Meterpreter and proceed to execute Kiwi from, namely EMUser.exe.
2. Time to Live
TTL > 64 it is most likely a Linux box
TTL > 128 it is most likely a Windows
TTL < 128 most likely some type of networking device.3. Some quick notes on organizing tooling:
Download and place the tool into /opt/ (e.g., Aquatone).
Execute the following command on the Aquatone binary:
ln -s /opt/aquatone/aquatone /usr/local/bin/aquatone
3. Reverse shell preferences:
External: Bind shell
Internal: Reverse shell
4. Microsoft has a great reference for .NET Framework & Windows OS Versions. We can then use a precompiled binary from SharpCollection to exploit the system.
Compile the binaries yourself.. Unless it's a CTF.
5. Performing password spraying with SprayCharles from my experience is more successful than using the SprayingToolkit. Ran into a situation on an engagement where multiple valid logins were reported as invalid by SprayingToolkit.
6. Kali Linux allows for multiple IP addresses to be set manually on an interface, allowing for you to set multiple callbacks in case one of your IP addresses gets banned. The following demonstrates a screenshot of this:
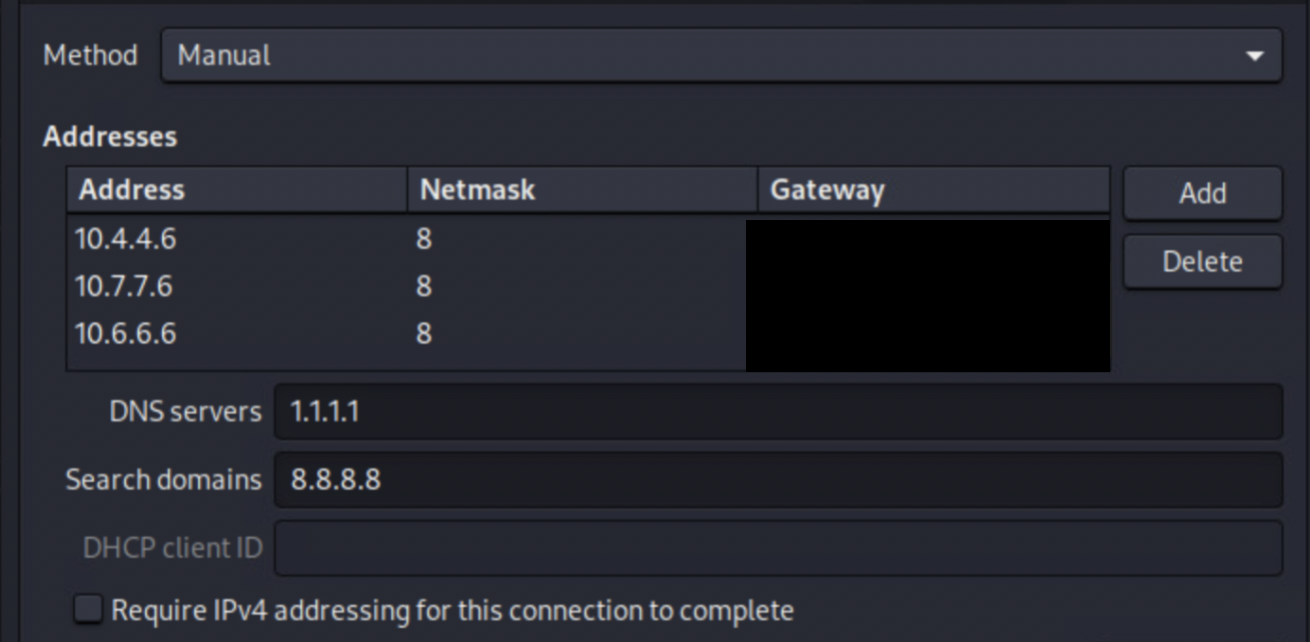
7. Download a Nessus scan via Metasploit:
8. Quick SSH tips:
Add SOCKS to an Existing SSH Connection
Forward a Port on an Existing SSH Connection
9. Make your life significantly easier when analyzing email headers with Message Header Analyzer.
10. Trying to make a high quality screenshot to illustrate commands used? Check out carbon.now.sh.
10. Don't know what a command does? There's no shame in that. For Linux check out ExplainShell and for PowerShell use ExplainPowershell.
11. Check the configuration of LAPS using a machine account per @HackingLZ, as it was noted that configurations are often messed up for them.
12. Your daily reminder that RDP local admin bruteforce has no rate limiting.
13. If you have a shell on a Windows host and need to check if your process is high integrity without sounding alarms, you can issue the following check:
14. A fun way to execte payloads is via a domains TXT record, the following command will run the provided payload:
15. Always perform content discovery both as an unauthenticated and authenticated user (provide cookies to tool of choice)
16. Trigger NTLM authentiction over HTTP from the command line:
Impacket's
wmiexec.pyis useful for lateral movement but is often detected. To potentially defeat detections, change the tgt share (-share C$) or use "-silentcommand".Leave Pcredz, Impacket SMB server, Responder (Analyze mode), etc running all the time. You never know when a random Domain Admin will try to auth to you over NTLM (agentless security products).
If you PWN a system during a penetration test (local admin privs) but still don't have a "domain user" - you can escalate privileges to SYSTEM and leverage the machine account.
Large password lists such as Rockyou2021 are mostly junk. Bigger ≠ better. Weakpass.com has several wordlists with Kaonashi being decent and https://weakpass.com/wordlist/1927 being one of the largest suggested as they're inflated with junk.
Last updated